Implement a Highly Available Azure VPN
I was recently working with a large public university to design an Azure network architecture that would be scalable, flexible, and highly available. The design we settled on used the Azure vWAN service and they wanted to connect to their physical campus using IPSec VPN tunnels. Their on premises gateway is a Palo Alto firewall appliance, and they are using BGP for dynamic routing. The design is fairly straightforward, but when we went to implement, we discovered there was little documentation to guide us on some particulars at the time. Here is the documentation I wish we had to design and implement a highly available Azure VPN solution to an on premises Palo Alto firewall.
Basic Active/Passive VPN Architecture
I’ll start with a basic active/passive VPN using static routes to help illustrate. Also, to keep this post more focused I’m going to illustrate with just a normal Virtual Network Gateway instead of Azure vWAN. They work the same, the interfaces just look a little different.
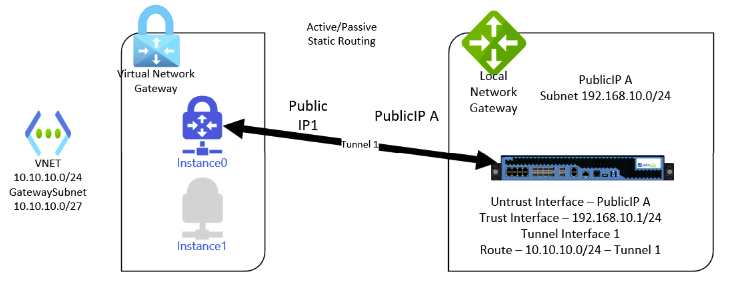
This is a simple design with a VNET in Azure with a gateway subnet. The gateway connects to an on premises Palo Alto firewall appliance (which Azure represents generically as a Local Network Gateway). Note that the VPN Gateway defaults to active/passive mode, which means there are two instances. If one instance fails or restarts, the Public IP and tunnel configuration will move to the other instance. Routes are statically assigned in this configuration (note the subnet configured in the Local Network Gateway and the route on the Palo Alto). This is sufficient for smaller/simpler organizations but will not meet the high uptime requirements or dynamic routing needs of enterprise organizations.
Note the Palo Alto tunnel interface does not need to have an IP assigned at all.
Active/Passive VPN with Dynamic Routing (BGP) Architecture
This is the next step in complexity and feature configuration. With this setup there are not redundant tunnels to protect from a failure from one of the gateway instances, but dynamic routing is configured.
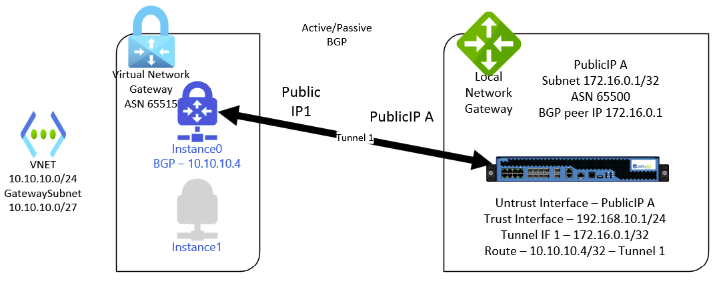
On the Azure gateway there is now an ASN assigned (starting at 65515) along with a private IP for BGP peering from the gateway subnet. Note that you can also assign a custom APIPA address for BGP peering in the 169.254.21.0-169.254.22.255 range. The local gateway is also assigned a BGP peering IP address with at least one static route to that peering address. On the Palo Alto, the BGP peering address can be assigned to the tunnel interface (or a loopback as we’ll see below) and there needs to be a route to the Azure peering address across the tunnel. I’m not going to go through the entire setup in greater detail because it is well documented elsewhere and fairly straightforward.
Palo Alto VPN with Dynamic Routing
Active/Active VPN with Dynamic Routing (BGP) Architecture
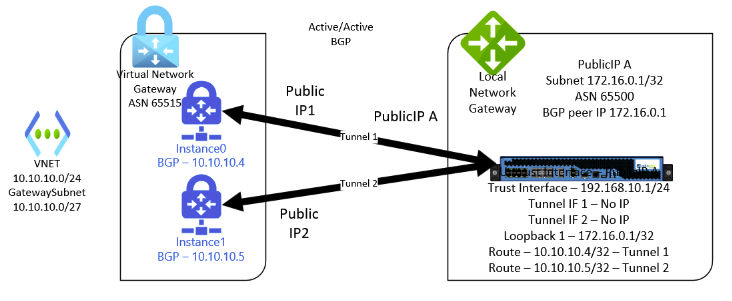
Finally, this brings us to the configuration we truly want. We can implement a highly available Azure VPN deployment with dynamic routing. In this configuration, both gateway instances are active and have tunnels established to the Palo Alto appliance to protect against failure. BGP is required in this scenario.

On the Azure side, there will now be two public IP addresses assigned along with two peering addresses (which can again be from the gateway subnet or custom APIPA addresses). On the Palo Alto, we need to configure two tunnel interfaces and two VPN tunnels. Neither tunnel interface needs an IP address assigned. The Palo Alto needs a route for each peering address on the respective tunnel as seen above. And the key:
The BGP peering address for the Palo Alto needs to go on a loopback interface!
This ensures that even if one of the tunnels is down, BGP peering can still occur on the same IP address across the other tunnel. The only documentation I could find at the time that suggested this can be found here:
Azure VWAN VPN Gateway High Availability Design
Since that project ended, Palo Alto put out a fantastic guide that covers this and way more here:
Palo Alto Azure Deployment Guide
Share this content:
I am a leader and solutions architect with over 10 years of hands on experience in private, public, and hybrid cloud technologies, networking, security, and data center management. My passion is to help clients gain agility and accelerate their business through IT modernization using cloud technologies.
I have consulted for some of the largest universities and corporations in the world on topics such as Azure Architecture, Infrastructure as Code, Azure Virtual Desktop, Application Hosting, Network Security, Identity Management, and much more.
Finally, I am actively involved in Christian ministry as a teacher and I strive to reflect the character of Jesus in every area of life.
The best place to contact me is on LinkedIn
You can subscribe to receive new posts via email.
Leave a Reply