How Azure Virtual Desktop Enables Zero Trust
This post is the second in a series where my goal is to show how AVD can help you achieve some of your key IT initiatives. My last post gave a high level overview of Azure Virtual Desktop and some of the key features and benefits. This time, I’ll dive deeper into an aspect of security for AVD to discuss how Azure Virtual Desktop enables a zero trust security model.
The Goal
As an IT Director or security leader in your organization, you know that the old model of “perimeter only IT security” is no longer sufficient. You can’t think only in terms of an internal secure network and an external insecure network any longer. In today’s security landscape, you have to focus on identity as the key security perimeter. You also have to assume breach. These are some of the key tenants of a zero trust security model.
In order to make your zero trust security model a reality, you know you need to ensure that all of your applications and data require authentication to access. You also want the authentication to be supported by strong security controls. Away you go, making sure that your databases, file shares, and applications have some form of authentication in place. Things are going great, until…
The Problem
You talk to the manager of one of the departments and they have that one application. You know, the one that is critical for their business. The one that has important data in it and does important things. It has a windows client application that allows the users to access it. And the authentication is either non-existent or terribly insecure. The long-term solution is to find/buy/build a new application or to refactor the existing application. But that takes a lot of time and money to accomplish. How can you secure your application and data now?
Azure Virtual Desktop Enables Zero Trust
A simple solution to this problem of protecting your application is to wrap it in another layer. If your application is a full windows client application, you are limited from using web application strategies like Azure Application Proxy. But you can install the application on a specific virtual machine that has strong protections.
Azure Virtual Desktop is perfectly suited to protect a weak application. When you connect to a virtual machine using Azure Virtual Desktop, the authentication is handled by Azure Active Directory (AAD). Azure Active Directory allows you to enforce multi-factor authentication (MFA), enforce access policies that limit where, when, or how something is accessed, and more. The diagram below shows how the Azure Virtual Desktop solution enables zero trust and how the AAD authentication layer combines with AVD to enhance security.
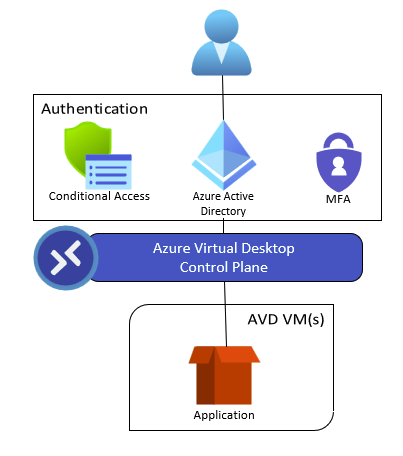
The user experience is also a key component of this solution. You don’t have to force users to log into a full separate desktop for just one application. You can deliver only the application as a window, similar to RemoteApp or Citrix, or the users can access the application or full desktop using a common web browser. This flexibility is important to making sure the user experience is a great fit for your unique users.
Conclusion
Information security is a hard job and there are always challenges along the road to improving the security posture of your organization. Nevertheless, pushing towards the zero trust security model is important to protecting your organization. Hopefully, this post has armed you with another tool to deal with the problem applications that are difficult to secure. Azure Virtual Desktop is a great solution to keep you moving ahead on the road to enabling zero trust.
Share this content:
I am a leader and solutions architect with over 10 years of hands on experience in private, public, and hybrid cloud technologies, networking, security, and data center management. My passion is to help clients gain agility and accelerate their business through IT modernization using cloud technologies.
I have consulted for some of the largest universities and corporations in the world on topics such as Azure Architecture, Infrastructure as Code, Azure Virtual Desktop, Application Hosting, Network Security, Identity Management, and much more.
Finally, I am actively involved in Christian ministry as a teacher and I strive to reflect the character of Jesus in every area of life.
The best place to contact me is on LinkedIn
You can subscribe to receive new posts via email.
Leave a Reply