How to Reduce Azure Firewall Costs
Azure Firewall is a great first party managed firewall service on Azure and it has seen tremendous growth. The one downside of Azure Firewall is its cost which is over $1,200/mo for the Premium SKU. Now don’t get me wrong, I think that price is actually pretty good for what it is, but what if there was a way to reduce Azure Firewall costs in certain scenarios? Read on as I impart to you the secret knowledge of how to reduce your Azure Firewall costs!
Deallocate Azure Firewall
The real crux of how to reduce costs is to not run the firewall 24/7. I’ll bet you didn’t know that was an option! There is no shutdown button for the Azure Firewall anywhere in the portal. There is, however, a way to stop the firewall with PowerShell while leaving all the configuration in place. This also works for VWAN Hubs that are secured with an Azure Firewall. As a bonus, this also works for Application Gateways / WAFs, but it is a little different.
Here is what a Firewall looks like when it is started:
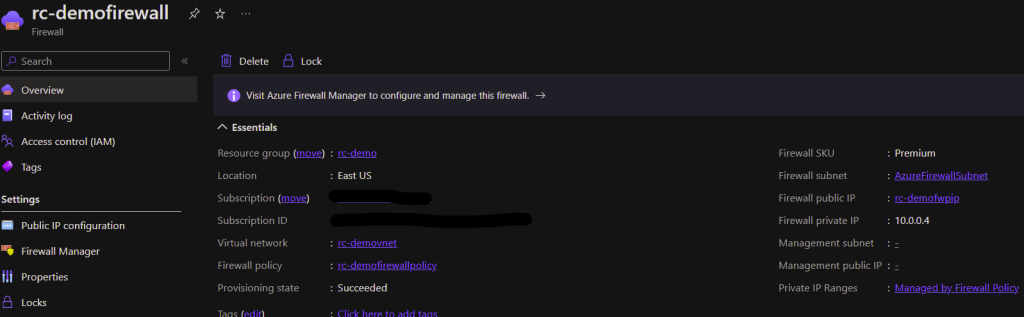
And here is what it looks like when it is stopped/deallocated:
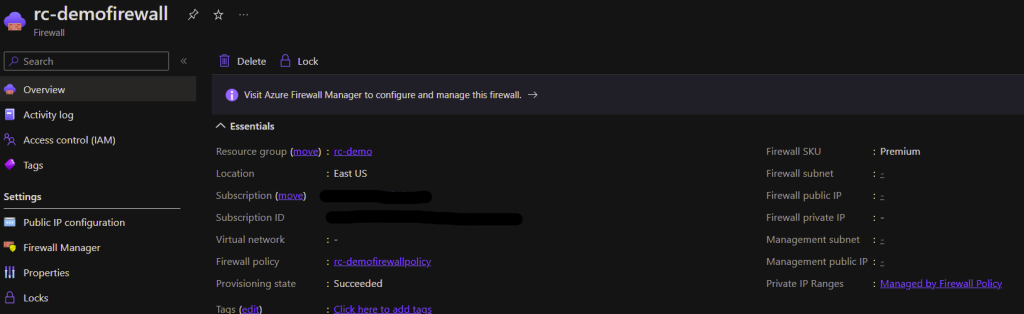
Here is a WAF that is started:
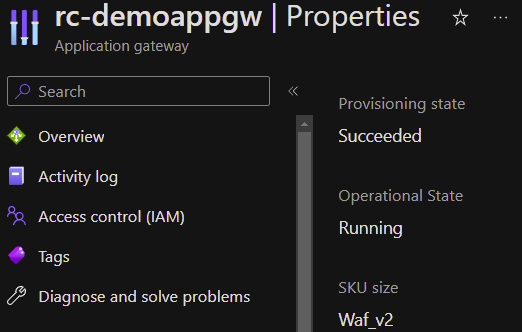
Here is a WAF that is stopped:
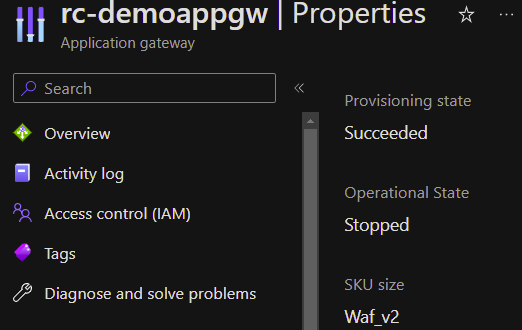
When to Stop Azure Firewall
When you stop an Azure Firewall or WAF it doesn’t function anymore so your application or network traffic won’t flow. There are only a handful of situations where you can get away with this since most production environments require 24/7 functionality (though there are a few exceptions out there).
A lab or development environment is one great scenario where you could shut down your Azure Firewall. You could save costs by shutting down your Firewall outside of business hours when you don’t expect any testing to occur. See below for how you could automate this. You could easily reduce your costs by over 50% in your lab environment using this method.
Another scenario where you can reduce costs by stopping your Azure Firewall is in a DR environment. If you have another region where you have cold spares of VMs or other services, that is a great opportunity to save Firewall costs. In an environment like this, you typically set up all your network components, replicate your VMs and data, then in an outage you power everything on. This could save over $1,200/mo. With Azure Firewall, you can manage all of your policies and keep them current, but keep the Firewall off along with your VMs. You could even orchestrate your Firewall starting as part of a DR failover process. See below for how to get started.
Stop and Start Your Azure Firewall with Automation
You can manually start/stop Azure Firewalls or Application Gateways using PowerShell, but it is even better if you can automate it. I created an Azure Automation account, granted the system assigned Managed Identity to have the IAM Contributor role to my Firewall resources, and then I created a runbook with the following PowerShell code:
connect-azaccount -identity
$firewall = Get-AzFirewall -Name "rc-demofirewall" -ResourceGroupName "rc-demo"
$vnet = Get-AzVirtualNetwork -Name "rc-demovnet" -ResourceGroupName "rc-demo"
$publicip = Get-AzPublicIpAddress -Name "rc-demofwpip" -ResourceGroupName "rc-demo"
$firewall.Deallocate()
$firewall | Set-AzFirewallTo start the firewall again you would do this:
connect-azaccount -identity
$firewall = Get-AzFirewall -Name "rc-demofirewall" -ResourceGroupName "rc-demo"
$vnet = Get-AzVirtualNetwork -Name "rc-demovnet" -ResourceGroupName "rc-demo"
$publicip = Get-AzPublicIpAddress -Name "rc-demofwpip" -ResourceGroupName "rc-demo"
$firewall.Allocate($vnet,$publicip)
$firewall | Set-AzFirewallOr if it is a secured virtual hub for a VWAN deployment it would look a little different to start:
$virtualhub = get-azvirtualhub -ResourceGroupName gbb-er-lab-we -name vwan-hub-ne
$firewall = Get-AzFirewall -Name "AzureFirewall_VWAN-Hub-NE" -ResourceGroupName "GBB-ER-LAB-WE"
$firewall.Allocate($virtualhub.Id)
$firewall | Set-AzFirewallAnd here is the code to start / stop an Application Gateway with a runbook:
connect-azaccount -identity
$appgw = Get-AzApplicationGateway -Name rc-demoappgw -ResourceGroupName rc-demo
Start-AzApplicationGateway -ApplicationGateway $appgw
## Or to Stop
connect-azaccount -identity
$appgw = Get-AzApplicationGateway -Name rc-demoappgw -ResourceGroupName rc-demo
Stop-AzApplicationGateway -ApplicationGateway $appgwAs I said above, you could easily use a Runbook like these on a schedule to only keep your Azure Firewall running during business hours for testing purposes. Or you could use them as part of a disaster recovery orchestration.
Conclusion
I hope this was a helpful explanation of when and how to save cost with Azure Firewall. Here is the documentation from Microsoft where you can see the commands from the source. And here is another great write-up of some of this information. If you want to read about some other news related to Azure Firewall head over here where I wrote about a new Azure Firewall SKU. I am interested to hear if you knew this functionality existed already or if this is the first you have heard of it. Also, please let me know if you have any other ideas about how to use this type of automation!
Share this content:
I am a leader and solutions architect with over 10 years of hands on experience in private, public, and hybrid cloud technologies, networking, security, and data center management. My passion is to help clients gain agility and accelerate their business through IT modernization using cloud technologies.
I have consulted for some of the largest universities and corporations in the world on topics such as Azure Architecture, Infrastructure as Code, Azure Virtual Desktop, Application Hosting, Network Security, Identity Management, and much more.
Finally, I am actively involved in Christian ministry as a teacher and I strive to reflect the character of Jesus in every area of life.
The best place to contact me is on LinkedIn
You can subscribe to receive new posts via email.
1 comment so far